Getting into the Pace 5268AC Router, part 1: Terminals and Hashes
I got stuck on my Casio SK-1 project and needed to take a break, so I started on another project I’ve been meaning to do.
I’ve had gigabit fiber service at my apartment in Atlanta for nearly two years through a major global telecom provider. The service itself has been pretty good, but one thing I didn’t like was the fact that I couldn’t use my own router, or put theirs into a proper “bridged” mode.
When trying to use my own router, even after cloning the MAC of theirs, I was unable to obtain a DHCP lease. By sniffing the traffic between the router and the OTN, I found that the router needed to use 802.1X authentication to communicate with the OTN. So, I decided to tear open the router.
At the front of the router, I found what appeared to be some sort of debug port via an edge connector with 14 pins, and I soldered some 30ga Kynar wire to each pin for further investigation.
When I first fired up the device, it took a while to come up, and I got a worrying error message. Fortunately, it seems that this was just temporary.
After a lot of trial-and-error, I identified the four pins required to get a good, working serial console on the device.
The pins on the debug port are labeled 1 to 16 (two are missing but pin count is still incremented), and these are the ones I ended up with, along with port settings:
115200 8-n-1 GND - Pin 02 RXD - Pin 13 TXD - Pin 15
At this point, my plan was to remove the Flash chip from the board and dump it, but thanks to the prior work of Jhutchins, I was able to find the URL to download the firmware for this device. I modified the URL to match the firmware version running on my device, and downloaded the firmware.
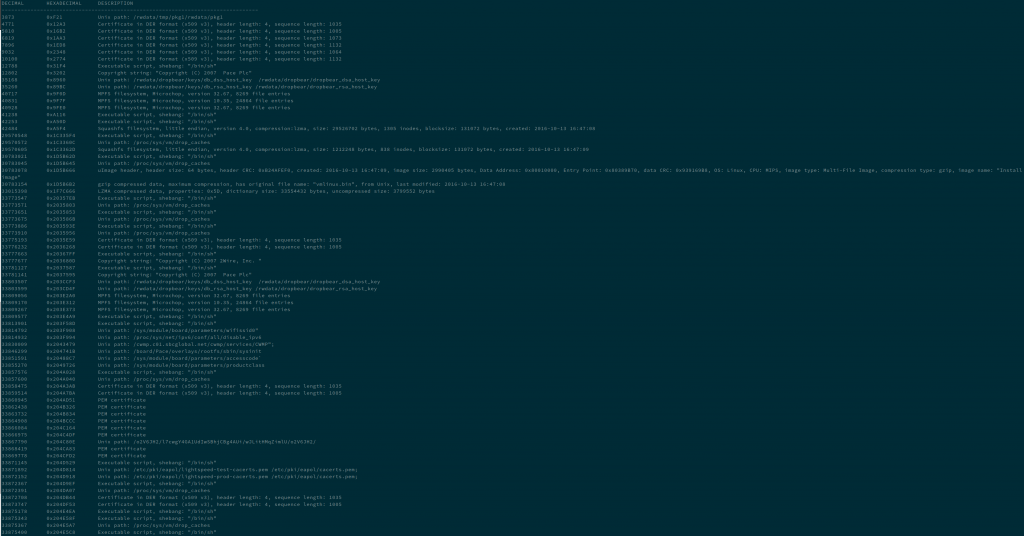
Once I had the ROM downloaded, I used binwalk to extract the contents of the file.
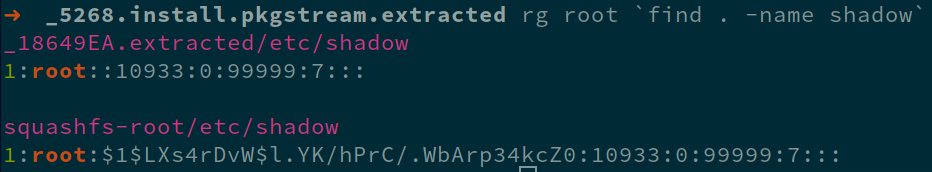
After a quick search, I found what looks like the md5crypt password hash for the root account on the device
Tomorrow, I’ll be borrowing the hashcat rig at my office to try and obtain the plaintext password and attempt to log in with it.